Exploited Vulnerability - UAP Cyber Siege 2025 - Final Round
In this challenge, participants were provided with a .pcapng file containing captured network traffic from a target machine. The goal was to analyze the traffic and uncover how an attacker managed to exploit a vulnerability in a WordPress-based web application.
Opening the .pcapng file with Wireshark, we can see that there are a lot of TCP & HTTP streams. On tcp.stream 13 reveals an interesting HTTP POST request. This request is made to the /wp-admin/admin-ajax.php endpoint, which is commonly used in WordPress for handling AJAX actions.
Within the stream, we notice a file being uploaded with the name cat.php. However, the content type is set as image/jpeg. Looking closer, the file starts with a fake image header GIF689a;, but the rest of the content is clearly a PHP payload. The payload uses eval(base64_decode(...)) to execute malicious code — a common method for web shells.
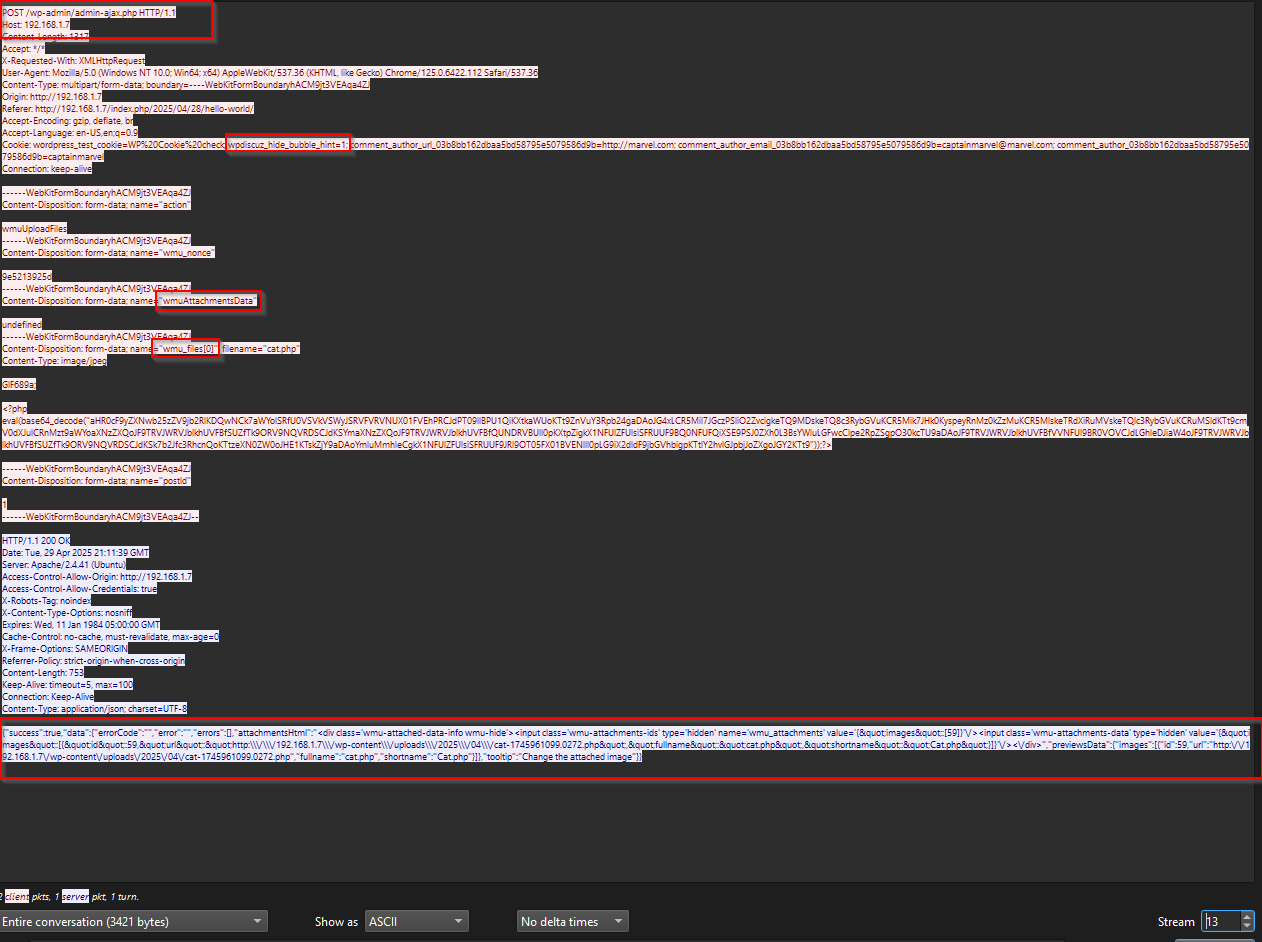
From the POST body, the action parameter is set to wmuUploadFiles, which is associated with the wpDiscuz plugin in WordPress. The plugin allows users to upload attachments in the comment section. The vulnerable server accepts and stores the uploaded PHP file without proper validation.
After uploading, the server responds with a JSON message containing the uploaded file URL:
http://192.168.1.7/wp-content/uploads/2025/04/cat-1745961099.0272.php
A quick Google search with the terms: wpdiscuz file upload RCE leads us to the known vulnerability CVE-2020-24186. This is a remote code execution vulnerability in wpDiscuz versions 7.0.0 to 7.0.4 that allows unauthenticated users to upload and execute arbitrary PHP files.
Just wrap the flag with the flag format & submit it. That's all. Thanks ❤
